Page 62 - Fister jr., Iztok, and Andrej Brodnik (eds.). StuCoSReC. Proceedings of the 2018 5th Student Computer Science Research Conference. Koper: University of Primorska Press, 2018
P. 62
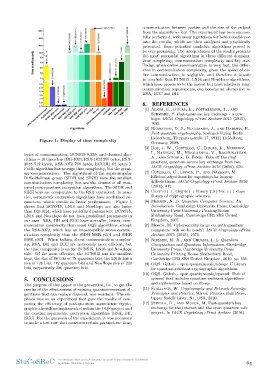
Figure 1: Display of time complexity communication between parties and the size of the output
from the algorithm - key. The experiment has been success-
bytes of communication, BCNS15 8,320, and classical algo- fully performed, with many repetitions for better confidence
rithms ∼ 10 times less (DH-1024, RSA-1024 256 bytes, RSA- into the results, which are then analyzed and graphically
2048 512 bytes, RSA-3072 768 bytes, ECCDH 64 bytes ). presented. Some potential candidate algorithms proved to
Frodo algorithm has average time complexity, but the great- be very promising. The interpretation of the results presents
est communication. The algorithms of the super-singular the most successful algorithms in three different domains:
Diffie-Hellman group (SIDH and SIKE) have the smallest time complexity, communication complexity and key size.
communication complexity, but are the slowest of all mea- Today, when online communication is very fast, the differ-
sured post-quantum encryption algorithms. The SIDH and ence in communication complexity, given the speed of on-
SIKE keys are comparable to the RSA equivalent. In prac- line communication, is negligible, and therefore it is safe
tice, asymmetric encryption algorithms have predefined pa- to conclude that BCNS15, LN16 and NewHope algorithms,
rameters, which results in faster performance. Figure 1 which have proven to be the fastest but have relatively large
shows that BCNS15, LN16 and NewHope are also faster communication requirements, can become an alternative to
than DH-1024, which have predefined parameters. BCNS15, RSA, ECC and DH.
LN16 and NewHope do not have predefined parameters in
our case. RSA, DH and ECC have a smaller, better, com- 6. REFERENCES
munication complexity than most OQS algorithms, except
the RSA-3072, which has an imperceptibly worse commu- [1] Alkim, E., Ducas, L., Po¨ppelmann, T., and
nication complexity than the SIDH MSR p501 and SIKE Schwabe, P. Post-quantum key exchange - a new
MSR p501. When talking about communication complex- hope. IACR Cryptology ePrint Archive 2015 (2015),
ity, RSA, DH and ECC are noticeably more efficient, but 1092.
the time complexity is on the BCNS15, LN16 and NewHope
side. Of the most effective, the BCNS15 has the smallest [2] Bernstein, D. J., Buchmann, J., and Dahmen, E.
keys, the size of 86 bits or 78 quantum bits, the LN16 has a Post-quantum cryptography. Springer-Verlag Berlin
size of 128 bits, 112 quantum bits and NewHope size of 229 Heidelberg, Tiergartenstraße 17, 69121 Heidelberg,
bits, respectively 206 quantum bits. Germany, 2009.
5. CONCLUSIONS [3] Bos, J. W., Costello, C., Ducas, L., Mironov,
The purpose of this paper is the prevention, i.e., to get the I., Naehrig, M., Nikolaenko, V., Raghunathan,
results of the effectiveness of existing quantum-resistant al- A., and Stebila, D. Frodo: Take off the ring!
gorithms that can replace classical, non-resistant. The em- practical, quantum-secure key exchange from lwe.
phasis was on an experiment that gave the results of com- IACR Cryptology ePrint Archive 2016 (2016), 659.
paring the efficiency of post-quantum asymmetric crypto-
graphic algorithms implemented within the OQS project and [4] Costello, C., Longa, P., and Naehrig, M.
the existing asymmetric encryption algorithms (RSA, DH, Efficient algorithms for supersingular isogeny
ECC). For the purposes of the experiment, it was necessary diffie-hellman. IACR Cryptology ePrint Archive 2016
to make a test case that measures certain parameters: time, (2016), 413.
[5] Crypto++. Crypto++ library 7.0 | free c++ class
library of cryptographic schemes.
[6] Mermin, N. D. Quantum Computer Science: An
Introduction. Cambridge University Press, Cambridge
University Press University Printing House
Shaftesbury Road, Cambridge CB2 8BS United
Kingdom, 2007.
[7] Mosca, M. Cybersecurity in an era with quantum
computers: will we be ready? IACR Cryptology ePrint
Archive 2015 (2015), 1075.
[8] Nielsen, M. A., and Chuang, I. L. Quantum
Computation and Quantum Information. Cambridge
University Press, Cambridge University Press
University Printing House Shaftesbury Road,
Cambridge CB2 8BS United Kingdom, 2010. pg. 555.
[9] OQS. Github - open-quantum-safe/liboqs: C library
for quantum-resistant cryptographic algorithms.
[10] OQS. Github - open-quantum-safe/openssl: Fork of
openssl that includes quantum-resistant algorithms
and ciphersuites based on liboqs.
[11] Stallings, W. Cryptography and Network Security:
Principles and Practice, 5th ed. Prentice Hall Press,
Upper Saddle River, NJ, USA, 2010.
[12] Stebila, D., and Mosca, M. Post-quantum key
exchange for the internet and the open quantum safe
project. In IACR Cryptology ePrint Archive (2016).
StuCoSReC Proceedings of the 2018 5th Student Computer Science Research Conference 64
Ljubljana, Slovenia, 9 October
from the algorithm - key. The experiment has been success-
bytes of communication, BCNS15 8,320, and classical algo- fully performed, with many repetitions for better confidence
rithms ∼ 10 times less (DH-1024, RSA-1024 256 bytes, RSA- into the results, which are then analyzed and graphically
2048 512 bytes, RSA-3072 768 bytes, ECCDH 64 bytes ). presented. Some potential candidate algorithms proved to
Frodo algorithm has average time complexity, but the great- be very promising. The interpretation of the results presents
est communication. The algorithms of the super-singular the most successful algorithms in three different domains:
Diffie-Hellman group (SIDH and SIKE) have the smallest time complexity, communication complexity and key size.
communication complexity, but are the slowest of all mea- Today, when online communication is very fast, the differ-
sured post-quantum encryption algorithms. The SIDH and ence in communication complexity, given the speed of on-
SIKE keys are comparable to the RSA equivalent. In prac- line communication, is negligible, and therefore it is safe
tice, asymmetric encryption algorithms have predefined pa- to conclude that BCNS15, LN16 and NewHope algorithms,
rameters, which results in faster performance. Figure 1 which have proven to be the fastest but have relatively large
shows that BCNS15, LN16 and NewHope are also faster communication requirements, can become an alternative to
than DH-1024, which have predefined parameters. BCNS15, RSA, ECC and DH.
LN16 and NewHope do not have predefined parameters in
our case. RSA, DH and ECC have a smaller, better, com- 6. REFERENCES
munication complexity than most OQS algorithms, except
the RSA-3072, which has an imperceptibly worse commu- [1] Alkim, E., Ducas, L., Po¨ppelmann, T., and
nication complexity than the SIDH MSR p501 and SIKE Schwabe, P. Post-quantum key exchange - a new
MSR p501. When talking about communication complex- hope. IACR Cryptology ePrint Archive 2015 (2015),
ity, RSA, DH and ECC are noticeably more efficient, but 1092.
the time complexity is on the BCNS15, LN16 and NewHope
side. Of the most effective, the BCNS15 has the smallest [2] Bernstein, D. J., Buchmann, J., and Dahmen, E.
keys, the size of 86 bits or 78 quantum bits, the LN16 has a Post-quantum cryptography. Springer-Verlag Berlin
size of 128 bits, 112 quantum bits and NewHope size of 229 Heidelberg, Tiergartenstraße 17, 69121 Heidelberg,
bits, respectively 206 quantum bits. Germany, 2009.
5. CONCLUSIONS [3] Bos, J. W., Costello, C., Ducas, L., Mironov,
The purpose of this paper is the prevention, i.e., to get the I., Naehrig, M., Nikolaenko, V., Raghunathan,
results of the effectiveness of existing quantum-resistant al- A., and Stebila, D. Frodo: Take off the ring!
gorithms that can replace classical, non-resistant. The em- practical, quantum-secure key exchange from lwe.
phasis was on an experiment that gave the results of com- IACR Cryptology ePrint Archive 2016 (2016), 659.
paring the efficiency of post-quantum asymmetric crypto-
graphic algorithms implemented within the OQS project and [4] Costello, C., Longa, P., and Naehrig, M.
the existing asymmetric encryption algorithms (RSA, DH, Efficient algorithms for supersingular isogeny
ECC). For the purposes of the experiment, it was necessary diffie-hellman. IACR Cryptology ePrint Archive 2016
to make a test case that measures certain parameters: time, (2016), 413.
[5] Crypto++. Crypto++ library 7.0 | free c++ class
library of cryptographic schemes.
[6] Mermin, N. D. Quantum Computer Science: An
Introduction. Cambridge University Press, Cambridge
University Press University Printing House
Shaftesbury Road, Cambridge CB2 8BS United
Kingdom, 2007.
[7] Mosca, M. Cybersecurity in an era with quantum
computers: will we be ready? IACR Cryptology ePrint
Archive 2015 (2015), 1075.
[8] Nielsen, M. A., and Chuang, I. L. Quantum
Computation and Quantum Information. Cambridge
University Press, Cambridge University Press
University Printing House Shaftesbury Road,
Cambridge CB2 8BS United Kingdom, 2010. pg. 555.
[9] OQS. Github - open-quantum-safe/liboqs: C library
for quantum-resistant cryptographic algorithms.
[10] OQS. Github - open-quantum-safe/openssl: Fork of
openssl that includes quantum-resistant algorithms
and ciphersuites based on liboqs.
[11] Stallings, W. Cryptography and Network Security:
Principles and Practice, 5th ed. Prentice Hall Press,
Upper Saddle River, NJ, USA, 2010.
[12] Stebila, D., and Mosca, M. Post-quantum key
exchange for the internet and the open quantum safe
project. In IACR Cryptology ePrint Archive (2016).
StuCoSReC Proceedings of the 2018 5th Student Computer Science Research Conference 64
Ljubljana, Slovenia, 9 October